powered by captain crunch security team
safe-mode: off (not secure)
home
basel 2.2
safe-mode: off (not secure) drwxrwxrwx
c99memoryl
c99shell [file on secure ok ]
c99shell v. 1.0 pre-release build #16
hacker
uid=99(nobody) gid=99(nobody) groups=99(nobody)
--[ c99shell v. 1.0 pre-release build #16
basel
c99shell v. 1.0 pre-release build
powered by captain crunch security team | http://ccteam.ru |
safe-mode : off ( not secured ) drwxrwxrwx
safe-mode: off (not secure) drwxrwxrwx c99shell
!c99shell v. 1.0 pre-release build #16!
--[ c99shell v. 1.0 pre-release build
-[ c99shell v. 1.0 pre-release build #16 powered by captain cru
/opt/zope/lib/python/zdaemon/zdrun.py
allintext:"safe-mode: off (not secure)"
allinurl:selfremove
basel documentation
c99memory.php
c99shell safe-mode : off ( not secured ) drwxrwxrwx
c99shell v. 1.0 pre-release build #16 powered by captain crunch
c99shell v. 1.0 pre-release uname
c99shell v. pre-release build
captain crunch security team
code safe-mode: off (not secure) drwxrwxrwx c99shell
drwxrwxrwx c99shell filetype:php
encoder bind proc. ftp brute sec. sql php-code feedback self re
encoder tools proc. ftp brute sec. sql php-code update feedback
home updir search buffer tools proc ftp brute sec sql self remo
how to restore using !c99memory v. 1.0 pre-release build #16!
intext:c99memory v. 1.0
intext:safe-mode: off (not secure)
intext:safe-mode: off (not secure) tooling
inurl:act=sql
name asc. size · modify · owner/group · perms action
php safe-mode drwxrwxrwx
php4 timezone database
powered by captain crunch security team drwxrwxrwx
powered by captain crunch security team | http://ccteam.ru
safe mode: off ( not secure )
safe mode: off (not secure)
safe-mode: off (not secure) / tmp/ drwxrwxrwx
safe-mode: off (not secure) site:pt
shell powered by captain crunch security team
site:www.astro.mat.uc.pt basel
uid= gid= groups= sql uname -a
uid=99 ( nobody ) gid=99 ( nobody )
uid=99(nobody) gid=99(nobody) groups=99(nobody)safe-mode: off
locus7shell
shell
kuwait hacker
php safe-mode bypass (list directories):
safe-mode: off (not secure)
safe-mode: off (not secure) drwxrwxrwx c99shell
startpar -f
hs_kuwait.php
lejeune interpolate
name asc. size · modify · owner/group · perms action
shell c99 ccteam.r
.phpact=f shell
00007458 zip
allintitle: \locus7shell\
allintitle: c99memoryl
allinurl:upload3.php
astro acrobat
basel stellar library
c99memory
c99memoryl
c99shell v. 1.0 pre-release build #16
class-efem
efemerides del 22 de abril
encoder bind proc. ftp brute sec. sql php-
encoder bind proc. ftp brute sec. sql php-code feedback
encoder bind proc. ftp brute sec. sql php-code update feedback
encoder tools proc. ftp brute sec. sql php-code update feedback
filetype:php shell
foreach (array(sortsql_sort) as $v)
i.s.s.w team ...
intitle:locus7shell
inurl:ftpquickbrute
inurl:php drwxrwxr-x ftp brute sql
lejeune interpolation
lejuene interpolate
lmgrd_start 47
mysqld usage of cpu suse httpd2-prefork
php echo getenv
php4 registered stream socket transports
powered by captain crunch filetype:php
powered by captain crunch security team drwxrwxrwx
safe-mode:
select action/file-type:
software make dir upload file safe-mode
uid=30(wwwrun) gid=8(www)
"uname -a","uid=","drwxr-xr-x","r57shell"
LOCUS7 SHELLlocus7shell
intitle:locus7shell
locus7shell filetype:php
locus7shell uname
allintitle: locus7shell
- locus7shell
intitle:- locus7shell
x2300 locus7shell
--[ x2300 locus7shell v. 1.0a beta modded by #!physx^ |
allintitle:- locus7shell
intitle: - locus7shell
safe-mode: off (not secure)
locus7shell 2008
shell x2300 locus7shell
.br - locus7shell
.us/images/0/588/mo_656_656.swf
allintext:--[ x2300 locus7shell v. modded by #!physx^
allintitle: - locus7shell
allintitle: locus7shell ext:php
allintitle:locus7shell
allintitle:locus7shell filetype:php
free locus7shell
ftp brute sec. sql php-code
inurl:act=sql
locus7s off secure
locus7s shell
ocus7shell apache
locus7shell edition 2008
locus7shell filetype: 'php'
locus7shell index:php
locus7shell linux 2008
locus7shell modified
php safe-mode bypass (list directories):
safe-mode: off (not secure) drwxrwxrwx locus7shell
%%% locus7shell
- locus7shell windows
--[ x2300 locus7shell v. 1.0a beta modded by #!physx^ | www.loc
--[ x2300 locus7shell v. modded by #!physx^ | www.locus7s.com |
--[ x2300 locus7shell v.1.0a beta modded by #!physx^ | www.locu
/locus7shell/
[enumerate] [encoder] [tools] [proc.] [ftp brute] [sec.] [sql]
allintext: locus7shell v. 1.0a beta
allintext:�safe-mode: off (not secure)�
allintitle: \locus7shell\
allinurl: .phpact=ls
apache aix aixthread_scope
ar ba locus7shell
basel
basel 3.1 library
basel interpolation
basel interpolation engine
basel spectra
c99memoryl
encoder bind proc. ftp brute sec. sql php-code feedback self re
filetype locus7shell
interpolation engine
intext:'' safe-mode:off (not secure)''
intitle:- locus7shell'
intitle:c99memoryl inurl:.php
intitle:locus7shell by filetype:php
intitle:locus7shell drwxr-xr-x
inurl:.phpact=ls
inurl:act intext:full hexdump
license.dat idl server bypass
locus7s uname
ocus7shell 2.0
locus7shell [file on secure ok ] drwxrwxrwx
locus7shell intext:x2300 intext:milw0rm.it enumerate uname
locus7shell inurl:php
locus7shell linux
locus7shell linux 2006
locus7shell safe-mode: off (not secure) drwxrwxrwx
locus7shell self remove drwxrwxrwx
locus7shell v. 1.0
locus7shell windows 2008
locus7shell-
make dir make file ok read files locus7shell
modded locus7shell
php safe-mode bypass (list directories)
php safe-mode bypass (read file)
php safe-mode bypass (read files)
safe-mode: apache uname -a: linux filetype:php
safe-mode: off (not secure) locus7shell
safe_mode: off drwxr-xr-x locus7shell
software: safe-mode: off (not secure) your ip: - server ip: [ft
suhosin 5.1.2
sybase aixthread_scope
uploads/ drwxrwxrwx
warning kernel may be alerted using higher levels safe mode
x2300 locus7shell download
x2300 locus7shell modified by #!physx^
x2300 locus7shell v. 1.0a
x2300 locus7shell v. 1.0a beta
FTP password:intitle:"index of" spwd.db passwd -pam.conf
filetype:bak inurl:"htaccess\passwd\shadow\htusers
filetype:inc dbconn
filetype:inc intext:mysql_connect
filetype:properties inurl:db intext:password
inurl:vtund.conf intext:pass -cvs
inurl:"wvdial.conf" intext:"password"
filetype:mdb wwforum
"AutoCreate:=TRUE password=*"
filetype:pwl pwl
filetype:reg reg +intext:"defaultusername" intext:"defaultpassword"
filetype:ref ref+intext:"internet account manager"
"index of/" "ws_ftp.ini" "parent directory"
filetype:ini ws_ftp pwd
inurl:/wwwboard
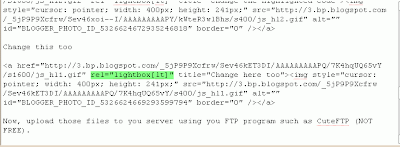
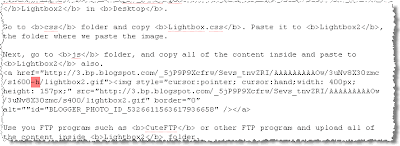
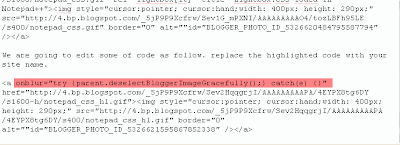
only copy the text in bold. copy and paste it in Google text box and pick your desired server.